Detonation
Here I performed controlled execution. For that I userd Wireshark, Burp Suite, INetSim and Procmon.
I opened malicious doc file and turned on macros.
After a while I turned off capturing in Procmon (Ctrl + E) and then I opened Process Tree (Ctrl + T). I expanded wininit.exe and searched PowerShell process started by wmiprvse.exe.
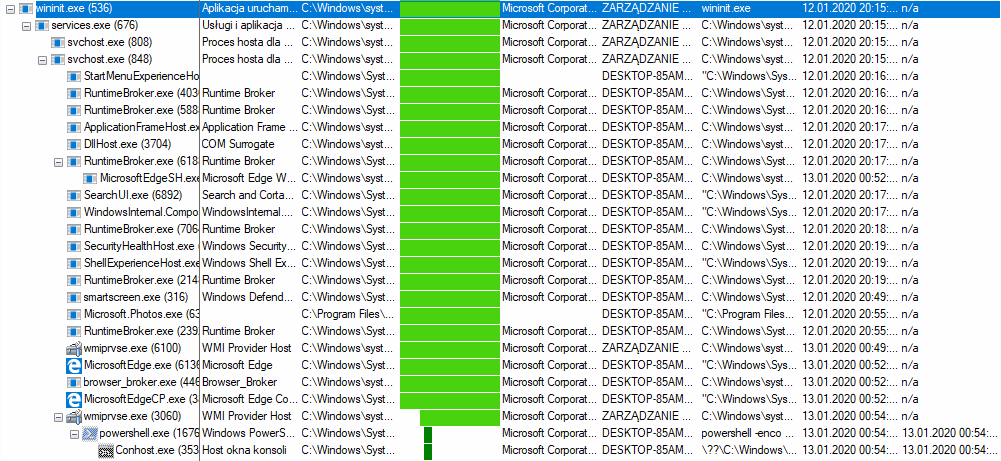

Then I right clicked on PowerShell process and selected option “Go To Event”. I closed Process Tree and in Procmon I right clicked on PowerShell entry and selected Properties.
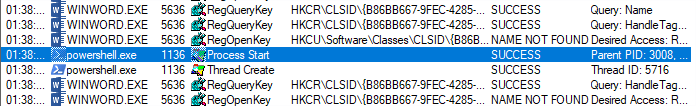
In “Event” and “Process” tab I found encoded PowerShell script, but I had already got it. Then I went to home directory and found there 126.exe.
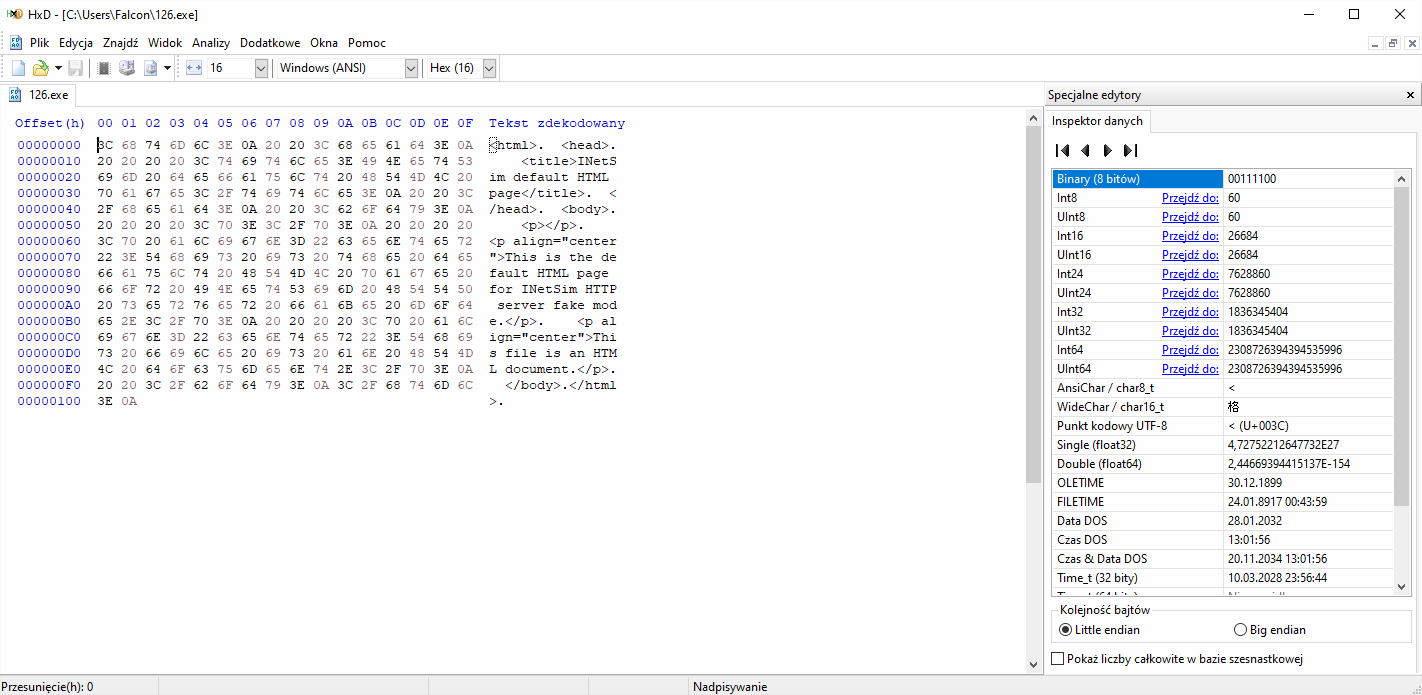
The file should contain html code from INetSim and it really did.
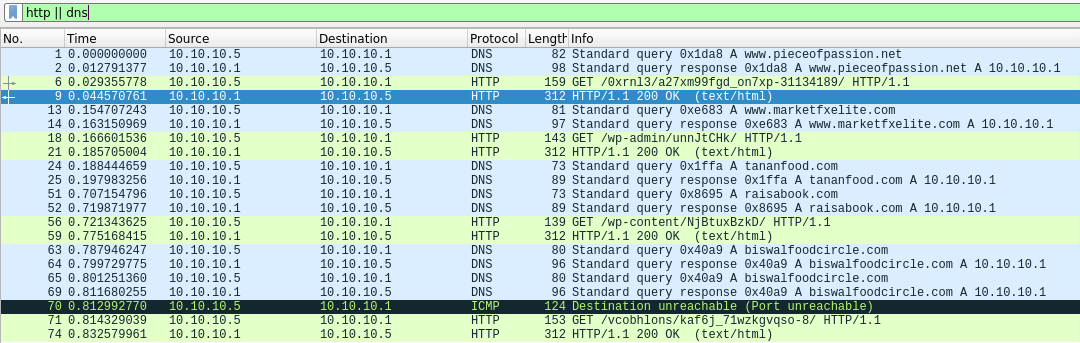
On my Linux machine I turned off INetSim and opened report file. The most interesting was the following part:
2020-01-12 18:53:52 DNS connection, type: A, class: IN, requested name: www.pieceofpassion.net
2020-01-12 18:53:52 HTTP connection, method: GET, URL: http://www.pieceofpassion.net/0xrnl3/a27xm99fgd_on7xp-31134189/, file name: data/http/fakefiles/sample.html
2020-01-12 18:53:52 DNS connection, type: A, class: IN, requested name: www.marketfxelite.com
2020-01-12 18:53:52 HTTP connection, method: GET, URL: http://www.marketfxelite.com/wp-admin/unnJtCHk/, file name: data/http/fakefiles/sample.html
2020-01-12 18:53:52 DNS connection, type: A, class: IN, requested name: tananfood.com
2020-01-12 18:53:53 DNS connection, type: A, class: IN, requested name: raisabook.com
2020-01-12 18:53:53 HTTP connection, method: GET, URL: http://raisabook.com/wp-content/NjBtuxBzkD/, file name: data/http/fakefiles/sample.html
2020-01-12 18:53:53 DNS connection, type: A, class: IN, requested name: biswalfoodcircle.com
2020-01-12 18:53:53 DNS connection, type: A, class: IN, requested name: biswalfoodcircle.com
2020-01-12 18:53:53 HTTP connection, method: GET, URL: http://biswalfoodcircle.com/vcobhlons/kaf6j_71wzkgvqso-8/, file name: data/http/fakefiles/sample.html
Additionaly Burp Suite captured that:
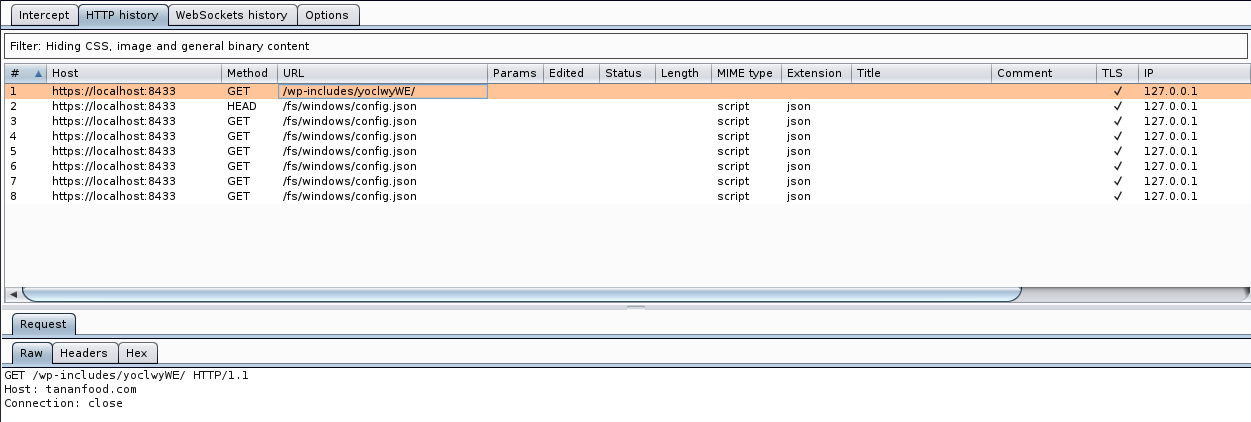
So domains that I had to check were:
http://www.pieceofpassion.net/0xrnl3/a27xm99fgd_on7xp-31134189/
http://www.marketfxelite.com/wp-admin/unnJtCHk/
http://raisabook.com/wp-content/NjBtuxBzkD/
http://biswalfoodcircle.com/vcobhlons/kaf6j_71wzkgvqso-8/
https://tananfood.com/wp-includes/yoclwyWE/
I used “http || udp” filter to gain information about packet traffic: